
INTRACOM DEFENSE Α.Ε.
Design of modern communication systems using “Cybersecurity by design’ frameworks”.
Overview
The cyberspace is defined as a complex environment resulting from the interaction of people, software, and services on the internet or any other publicly accessible network through interconnected systems, devices, and networks. Cybersecurity covers various security areas in cyberspace, such as information security, application security, network and internet security, and critical infrastructure security.
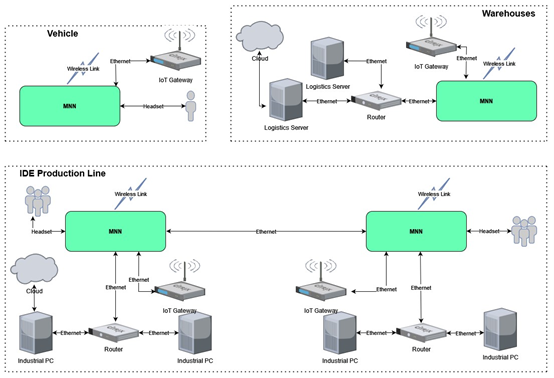
The solution aims to provide a methodology for developing secure products based on cybersecurity by design. It also involves implementing this methodology in the company’s product, MNN, which is a version of WiSPR TMN for civilian/commercial applications.
This particular product is a communication system capable of connecting to a wide range of wireless and other devices. The application of “cybersecurity by design” methodology to a network product with interactive features in real-time, such as MNN, demonstrates an exemplary scenario suitable for use in the context of Industry 4.0.
The term “cybersecurity by design” refers to a design and implementation process of the system that has incorporated all necessary security requirements into the system’s specifications for the smooth operation and protection of the system, recognizing security as an integral part of the whole product development lifecycle.
The chosen “cybersecurity by design” methodology is based on the “Common Criteria” methodology, which provides an established and internationally recognized framework for the evaluation and certification of security features in information technology products and systems. The methodology includes the following stages:
- Analysis of the system under evaluation (Target Of Evaluation – TOE)
- Extraction of security requirements
- Threat modeling
- Risk assessment
Services
The proposed approach for providing a methodology for the development of secure products consists of the following main steps that should be followed during the development stage of a product for which resilience to cyber-attacks is of primary concern:
- Analysis of the system under evaluation
- General system description and definition of the security problem
- Use case scenario definition
- System’s interfaces definition
- Security Requirements definition
- Security problem definition
- Assets Identification
- Security assumptions definition
- Security threats description
- Security objectives formation
- Organizational controls definition
- Security Functional Requirements (SFR) definition
- Threat Modeling
- Critical system resources recording
- Security roles definition
- Security-related function identification
- Functional security requirements formation
- Organizational measures
- Security assumptions
- Identification of potential threats
- Creation of Data Flow Diagrams (DFD)
- Risk Assessment
- Application of the aforementioned steps to an actual product
Benefits
- Proactive Risk Management: Identifying and addressing security aspects from the beginning helps in minimizing risks and addressing necessary cybersecurity issues sustainably and cost-efficiently
- Cost Efficiency: Incorporating security aspects into the design from the start minimizes the need for elaborate adjustments afterwards, which can be more costly
- Reduced Vulnerabilities: Designing with security in mind from the outset can help reduce the likelihood of leaving vulnerabilities in the product that may not be noticed until later on
- Resilience to Cyber Attacks: Security measures can be integrated into the system design and implemented at different levels, making the system highly resilient to various types of attacks.
- Confidence and Trust: Security by Design can add confidence to the project and promote a positive security culture, where cybersecurity is seen as a shared responsibility
- Compliance and Reputation: Building products with security in mind from the start can help ensure compliance with regulations and standards, as well as enhance the organization’s reputation for taking security seriously
- Long-term Cost Savings: While there may be initial adjustments to budgets and deadlines, consistent implementation of a security policy from the beginning can prevent costly interruptions to day-to-day operations and potential security breaches in the future
Value Proposition
The value of the proposition “Cyber Security by Design” is significant.
It involves integrating security measures into the design and development of networking products from the outset, rather than as an afterthought. This approach helps to ensure that security is a fundamental aspect of the product, leading to improved protection against cyber threats.
It also reduces the need for costly retrofits or security patches later on. The concept is particularly crucial in critical infrastructure and industrial control system environments, where the consequences of a cyber-attack can be severe.
Implementing cyber security by design can enhance the resilience of networking products and contribute to overall system reliability and safety.
Additionally, it can provide a competitive advantage and a strong value proposition for businesses, demonstrating a commitment to security and risk management.

Το έργο Agile4.0-Cluster υλοποιείται στο πλαίσιο της Δράσης ΣΥΝΕΡΓΑΤΙΚΟΙ ΣΧΗΜΑΤΙΣΜΟΙ ΚΑΙΝΟΤΟΜΙΑΣ/ ΣΣΚ και συγχρηματοδοτείται από την Ευρωπαϊκή Ένωση και εθνικούς πόρους μέσω του Ε.Π. Ανταγωνιστικότητα, Επιχειρηματικότητα & Καινοτομία (ΕΠΑνΕΚ).
Το έργο ξεκίνησε τον Αύγουστο του 2020 και αναμένεται να ολοκληρωθεί τον Αύγουστο του 2022.
Επιστημονικός υπεύθυνος είναι ο Δρ. Δημήτριος Τζοβάρας από το EKETA / ΙΠΤΗΛ.
Επικοινωνία
-
Ινστιτούτο Τεχνολογιών Πληροφορικής και επικοινωνιών
Εθνικό Κέντρο Έρευνας & Τεχνολογικής Ανάπτυξης,
6o χλμ Χαριλάου - Θέρμης, 57001, Θεσσαλονίκη - Dimitrios.Tzovaras@iti.gr
- +30 2311 257 701-3